User attribute basics
Can I use user attributes to control data access?
Can I use user attributes to control data access?
Yes. User attributes can be used in a few ways to control data access:
-
Access filters, which allow you to restrict the rows of data a user can access within a topic. Access filters apply the values assigned on a user attribute to the
WHEREclause of every SQL query a user runs, filtering out to only the data designated to that user:Filter by brand_name -
Access grants, which define topic- and field-level permissions. Omni will map a user’s attribute value to a corresponding allowed value and determine if the user has the necessary permissions to access that topic or field:
Grant access for user group
-
Fields. User attributes can be referenced in fields using Mustache syntax, for example:
{{ omni_attributes.<attribute-name> }}. This construct can be used to:- Provide conditional access to a field, or
-
To hash a field based on a user attribute. This can be done by using a
CASEstatement in the SQL definition for a field. For example, the followingname_hiddenandname_hashedexamples demonstrate how to use user attributes to hide or hash a name field as an alternative to using access grants to remove access entirely:Hide or hash field based on user attribute
Can I use user attributes to dynamically change database connections?
Can I use user attributes to dynamically change database connections?
Yes. User attributes can be used to parameterize the connection queries run against while in an Omni branch. Refer to the Dynamically switching database environments guide for more information and setup steps.
Can I use user attributes to route users to tenant-specific models?
Can I use user attributes to route users to tenant-specific models?
Yes. Shared extension models use user attributes to route users to the correct model extension. You define a mapping in the parent model’s
dynamic_shared_extensions parameter that links user attribute values to specific extensions.Can I use user attributes to create dynamic content?
Can I use user attributes to create dynamic content?
Yes. There are a few ways to do this:
- Dashboard Markdown tiles. You can use user attributes in dashboard Markdown tiles with Mustache syntax. For example,
{{metadata.userAttributes.<user_attribute>.values}}would return the value of the specified user attribute. - Dashboard deliveries. User attributes can be used to personalize deliveries, including messages (where supported) and the data included in the delivery.
Does Omni have any system (default) user attributes?
Does Omni have any system (default) user attributes?
Yes. Refer to the Default system attributes section for more information.
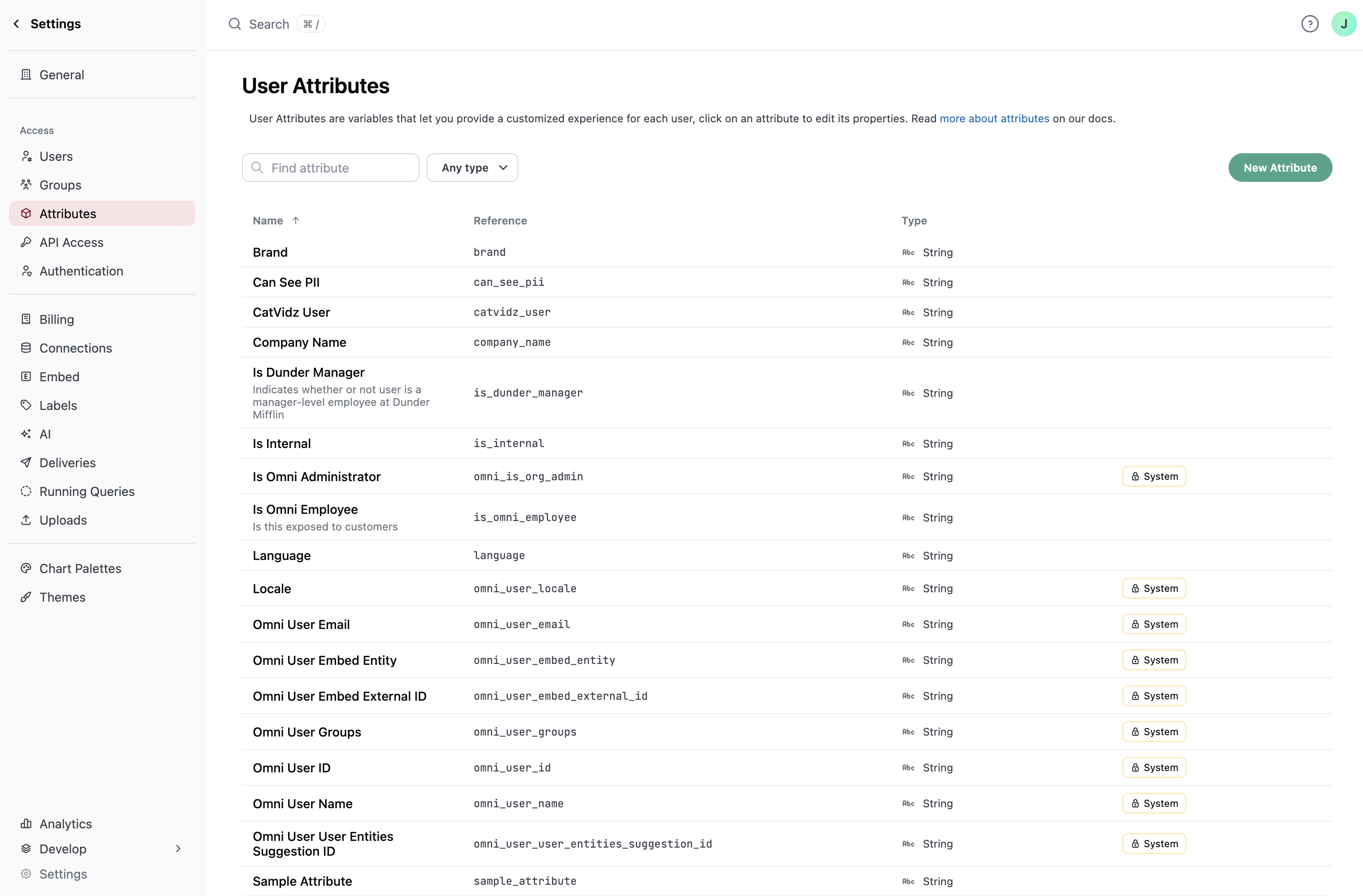
Creating user attributes
Organization Admin permissions are required to create new custom attributes.
- Name: The name of the user attribute, how it will be displayed in the UI
- Reference: How the attribute will be referenced in code, such as in the model
- Type: Used to check that valid values are assigned to users. String and Number data types are allowed.
- Multiple values: Specifies whether multiple values can be assigned to a user for this attribute
- Description: Explanation of the attribute or how it will be used
- Default value: Optionally, set a default value that all users will inherit if a value is not directly assigned to them
Assigning values to individual users
After defining a user attribute, assign a value for each user:- Click the Users tab.
- Click Edit Value for the user you want to assign the value to.
- Enter the new value:
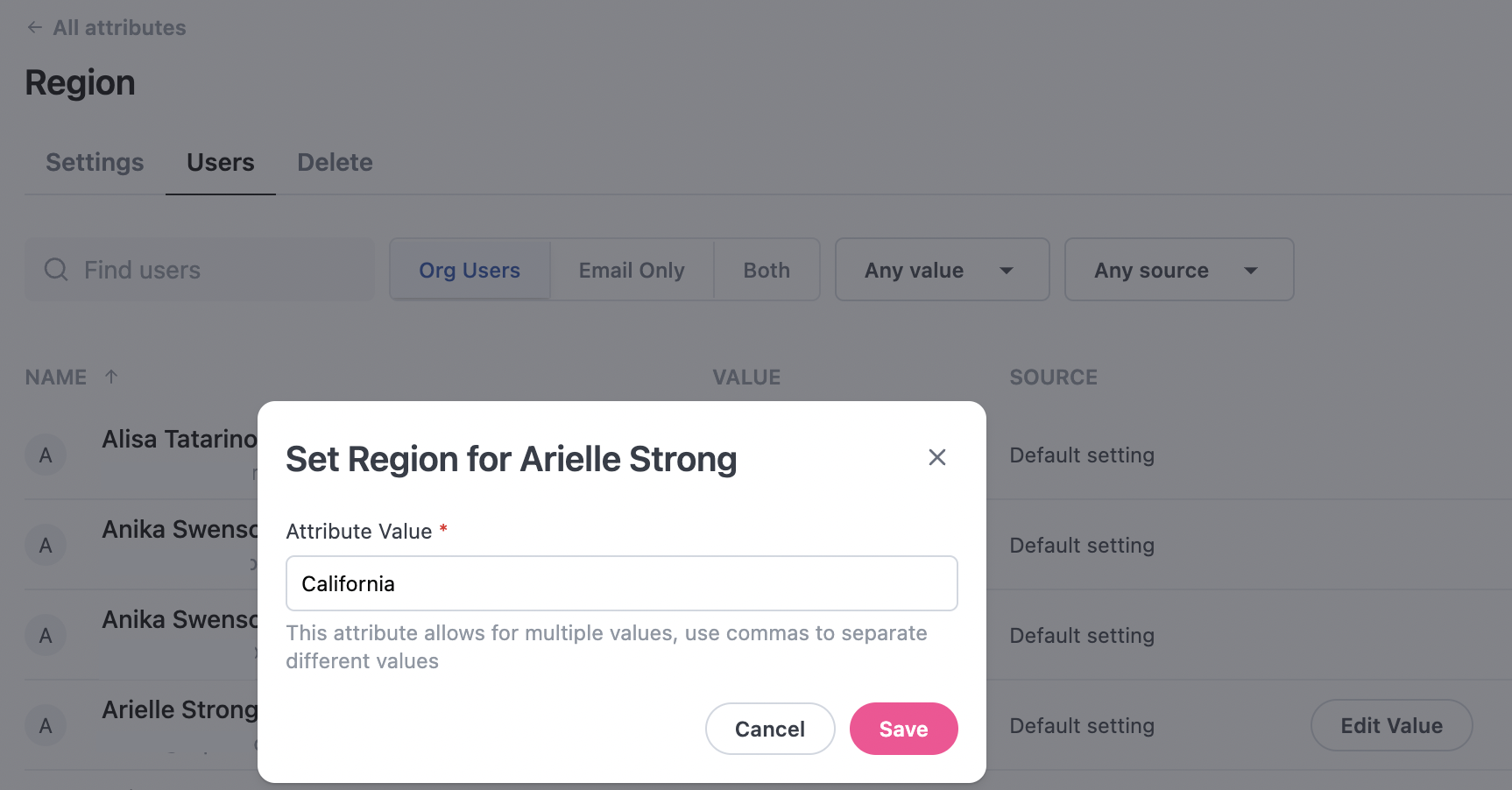
- Click Save.
Default system user attributes
System attributes are read-only.
If
true, the user is an Organization Admin.The user’s email address.
The user’s embedded entity name. For example,
Blobs R UsThe user groups that the user is a member of. The value will be a comma-separated list of user group names, for example
Blob Sales, Blob MarketingA unique identifier for the user. For example,
91abbe19-b0de-4537-bc62-cec1d95420c9The user’s locale code. Possible values are:
See the Localization guide for more information.
| Locale code | Language |
|---|---|
en-US | English (default) |
de-DE | Deutsch (Deutschland) |
es-CL | Español (Chile) |
es-ES | Español (España) |
fr-FR | Français (France) |
he-IL | עברית (ישראל) |
ja-JP | 日本語 (日本) |
The user’s name. For example,
Blob Ross or Blobby PartonThe user’s timezone, which is set using the Query timezone setting on the user’s profile. For example,
UTC or America/Los_Angeles
