Connection permission basics
Who can define connection permissions?
Who can define connection permissions?
Organization Admins and users who have Connection Admin permissions for a connection can define connection permissions.
What are the connection roles?
What are the connection roles?
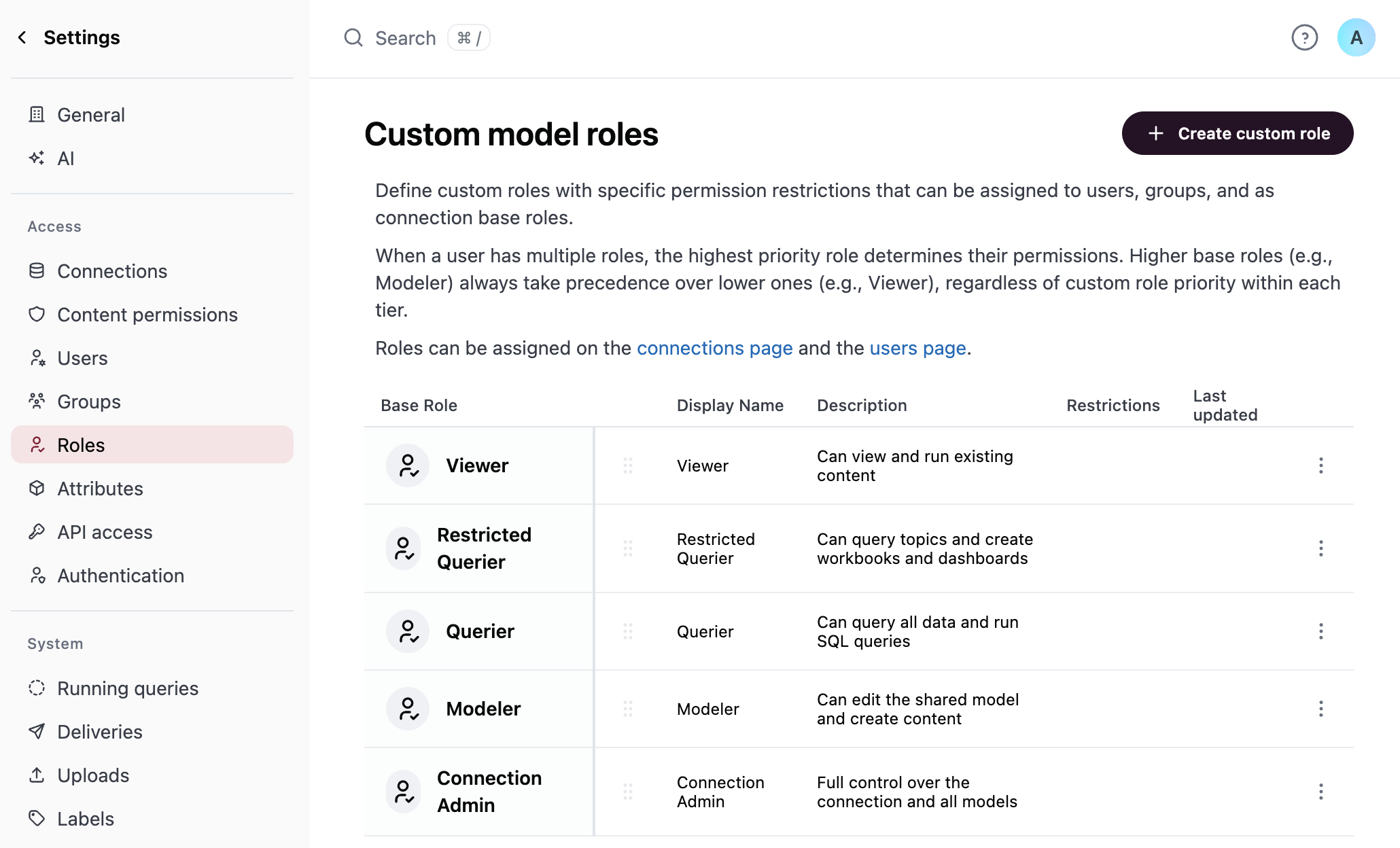
Omni currently supports five connection roles, ordered from the least permissive to the most permissive:
- No access
- Viewer
- Restricted Querier
- Querier
- Modeler
- Connection Admin
Can default permissions be applied to a connection?
Can default permissions be applied to a connection?
Yes. Using the Base access setting, you can assign the minimum role users will have for the models in the connection. More permissive roles can be set in the connection’s Model access section. Note: The base role will override a less permissive role set in the Model access section.
Can permissions be set at the model level?
Can permissions be set at the model level?
Yes! In the Model access section, you can assign granular permissions to users and user groups for specific models.
What permissions should I set to do [thing]?
What permissions should I set to do [thing]?
It depends on what you want to achieve! Do you want to lock everything down, or only restrict access for some things? Or perhaps it varies by team or dataset?In the Common permissions scenarios guide, we’ve outlined some common scenarios and how to use permissions to achieve the desired result. For example, limiting access to folders based on the team a user belongs to.
Do connection permissions impact a user's license type?
Do connection permissions impact a user's license type?
Yes. Refer to the User license types section for more information.
Defining permissions for a connection
Organization Admin or Connection Admin permissions for the connection are required to define connection permissions.
- Click Settings > Connections.
- Click the connection.
- Click the connection’s Permissions tab. On this page, you can define default access for the connection (Base access role) and assign permissions to users and user groups for specific models (Model access).
Testing data access
As you assign connection roles to users, you can impersonate them to test what users can see. This can be helpful in preemptively surfacing access warnings, which will display when users attempt to access specific types of content. Refer to the Access warnings guide to learn what an access warning is and how to resolve it.License types
Omni’s licensing structure has three tiers: Viewer, Standard, and Administrator/Developer. To calculate a user’s license type, Omni looks at:- The user’s highest Connection role across all connections, and
- Whether the user is an Organization Administrator. These users will have an Administrator license by default.
| License type | Connection role | Permissions |
|---|---|---|
| None | No Access | ❌ Cannot view content built on the connection ❌ Cannot query (topics) ❌ Cannot use SQL queries ❌ Cannot modify shared model files ❌ Cannot modify connection settings |
| Viewer | Viewer | ✅ Can view dashboards built on topics ❌ Cannot query topics ❌ Cannot use SQL queries ❌ Cannot modify shared model files ❌ Cannot modify connection settings |
| Standard | Restricted Querier | ✅ Can create, edit, and view workbooks and dashboards ✅ Can query topics (UI and AI) ❌ Cannot use SQL queries ❌ Cannot modify shared model files ❌ Cannot modify connection settings |
| Standard | Querier | ✅ Can create, edit, and view workbooks and dashboard ✅ Can query topics (UI and AI) ✅ Can use SQL queries ❌ Cannot modify shared model files ❌ Cannot modify connection settings |
| Admin/Developer | Modeler | ✅ Can create, edit, and view workbooks and dashboards ✅ Can query topics (UI and AI) ✅ Can use SQL queries ✅ Can modify shared model files ❌ Cannot modify connection settings |
| Admin/Developer | Connection Admin | ✅ Can create, edit, and view workbooks and dashboards ✅ Can query topics (UI and AI) ✅ Can use SQL queries ✅ Can modify shared model files ✅ Can modify connection settings |
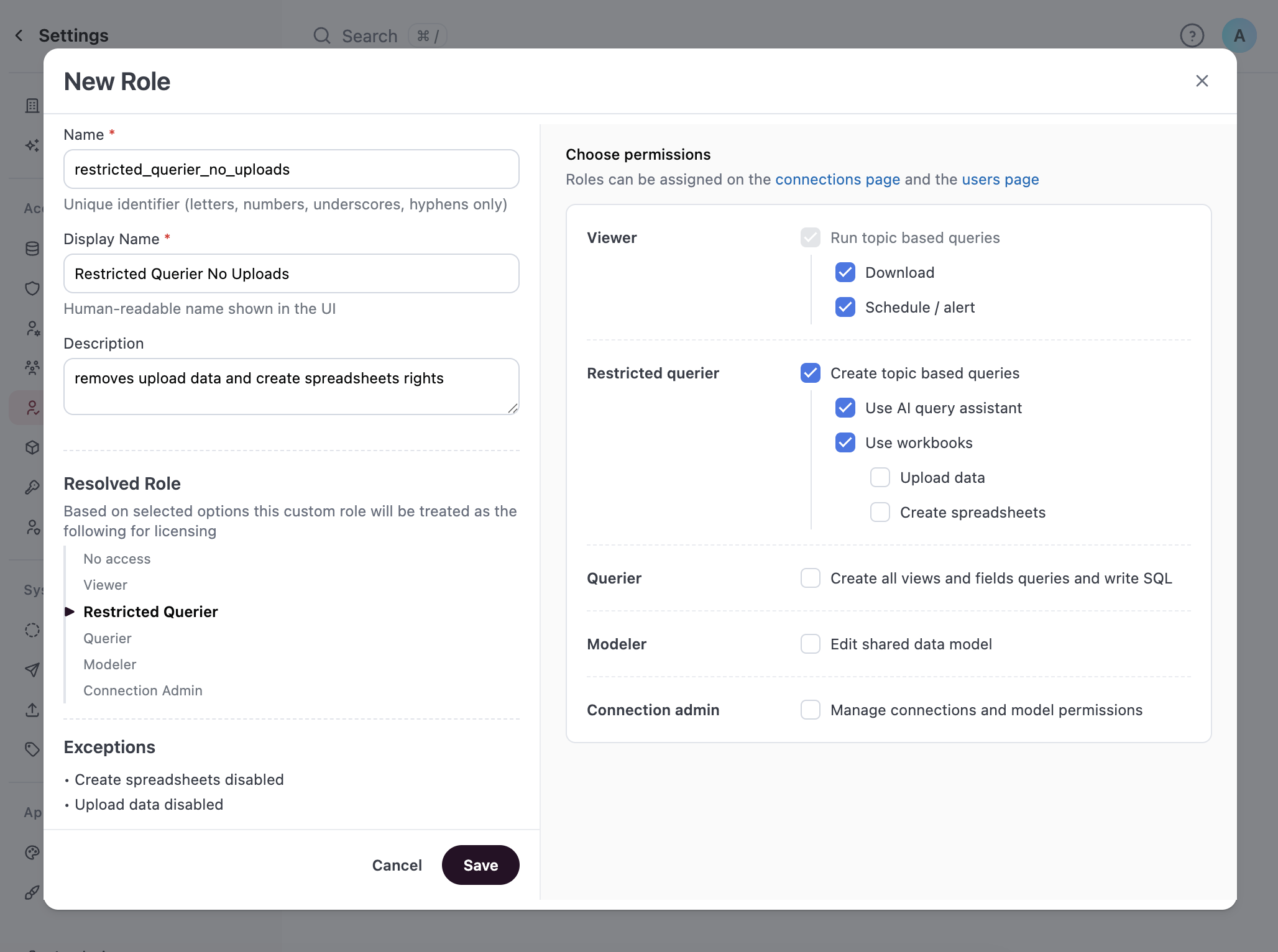
Custom Roles
Admins can define custom model roles to more granularly define permissions.